The Password Policies Page of the configuration editor allows you to edit the server's password policies. See also IETF draft-behera-ldap-password-policy-10 for a detailed description of the password policy configuration.
Here's what the Password Policies page looks like:
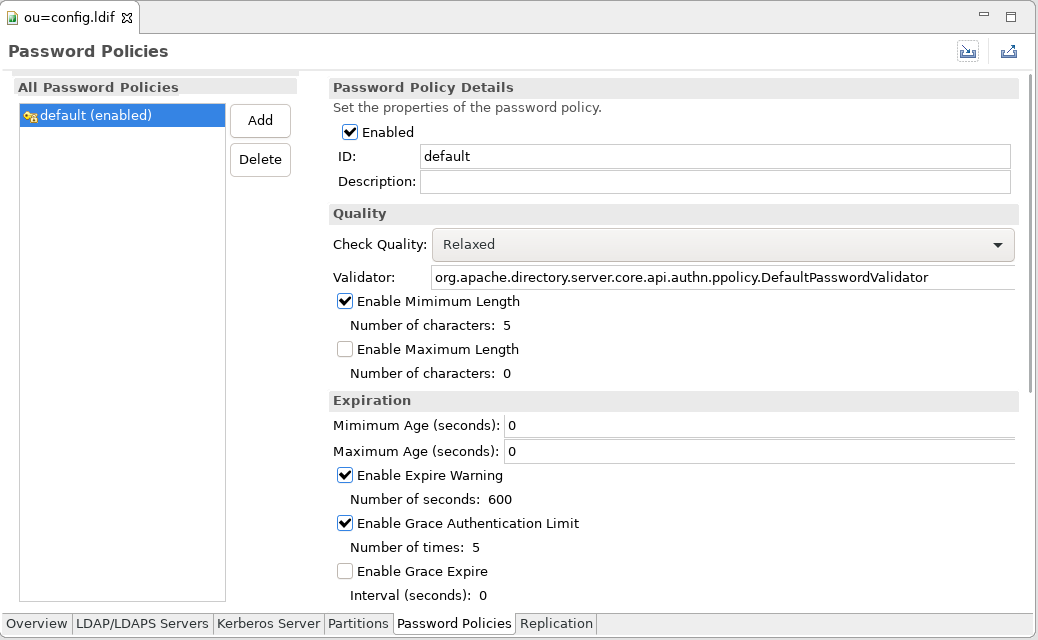
The page is divided vertically in two parts.
The left side of the page shows the password policies defined on the server. This is where you can add or delete a policy.
The right side of the page display and lets you edit the details of the selected password policy in the left side.
Check the Enabled checkbox to enable the password policy.
An ID is mandatory for the password policy.
An Description is optional for the password policy.
Check Quality defines which quality level a new password must fulfil. One of the following options can be chosen:
- Disabled - Don't check the password
- Relaxed - Check the password and accept passwords that can't be checked (hashed passwords)
- Strict - Check the password but reject passwords that can't be checked (hashed passwords)
Validator Defines the class that implements PasswordValidator interface (default org.apache.directory.server.core.api.authn.ppolicy.DefaultPasswordValidator).
Check Enable Minimum Length to enable and specify the minimum password length.
Check Enable Maximum Length to enable and specify the maximum password length.
Minimum Age defines the number of seconds that must elapse between modifications to the password.
Maximum Age defines the number of seconds after which a modified password will expire. Default value is 0, does not expire. If not 0, the value must be greater than or equal to the value of the minimum age.
Check Enable Expire Warning to enable and specify the number of seconds before password expiration a warning message will be returned to an authentication user.
Check Enable Grace Authentication Limit to enable and specify the how often an expired password can be used to authenticate.
Check Enable Grace Expire to enable and specify the number of seconds for the grace period.
Check Enable Must Change to enforce that the password must be changed by the user after a password reset.
Check Enable Allow User Change to allow users to change their own password.
Check Enable Safe Modify to enforce that the existing password must be ent when changing the password.
Check Enable Lockout to enable password lockout.
Lockout Duraton defines the number of seconds that the password cannot be used to authenticate due to too many failed bind attempts.
Maximum consecutive Failrues defines the number of consecutive failed bind attempts after which the password may not be used to authenticate.
Check Enable Maximum Idle to enable and specify the number of seconds an account may remain unused before it becomes locked.
Check Enable In History to enable and specify the maximum number of used password history is preserved.
Minimum Delay defines the number of seconds to delay responding to the first failed authentication attempt. Default value 0, no delay
Maximum Delay defines the maximum number of seconds to delay responding to the first failed authentication attempt.